Compare commits
2 commits
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
4eb3121ed3 | ||
|
|
5a54353159 |
3 changed files with 16 additions and 19 deletions
23
README.md
23
README.md
|
|
@ -2,6 +2,8 @@
|
||||||
|
|
||||||
Simple web UI to manage OpenVPN users, their certificates & routes in Linux. While backend is written in Go, frontend is based on Vue.js.
|
Simple web UI to manage OpenVPN users, their certificates & routes in Linux. While backend is written in Go, frontend is based on Vue.js.
|
||||||
|
|
||||||
|
Originally created in [Flant](https://flant.com/) for internal needs & used for years, then updated to be more modern and [publicly released](https://blog.flant.com/introducing-ovpn-admin-web-interface-for-openvpn/) in March'21. Your contributions are welcome!
|
||||||
|
|
||||||
***DISCLAIMER!** This project was created for experienced users (system administrators) and private (e.g., protected by network policies) environments only. Thus, it is not implemented with security in mind (e.g., it doesn't strictly check all parameters passed by users, etc.). It also relies heavily on files and fails if required files aren't available.*
|
***DISCLAIMER!** This project was created for experienced users (system administrators) and private (e.g., protected by network policies) environments only. Thus, it is not implemented with security in mind (e.g., it doesn't strictly check all parameters passed by users, etc.). It also relies heavily on files and fails if required files aren't available.*
|
||||||
|
|
||||||
## Features
|
## Features
|
||||||
|
|
@ -19,16 +21,16 @@ Simple web UI to manage OpenVPN users, their certificates & routes in Linux. Whi
|
||||||
### Screenshots
|
### Screenshots
|
||||||
|
|
||||||
Managing users in ovpn-admin:
|
Managing users in ovpn-admin:
|
||||||
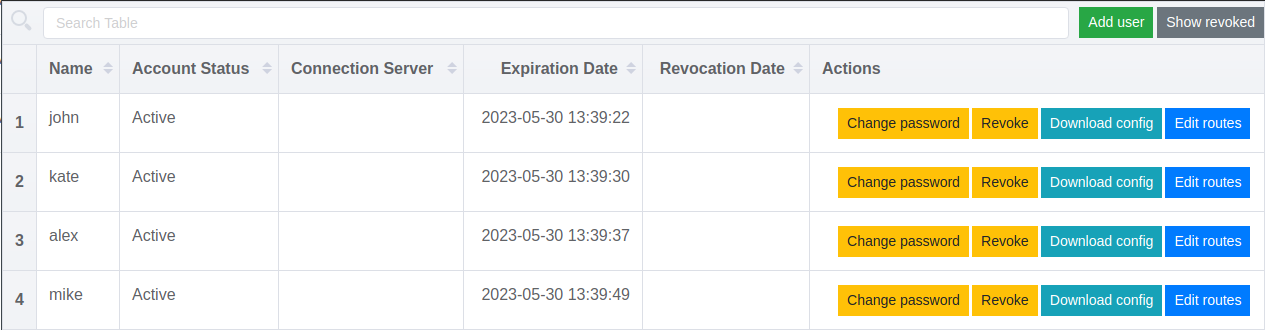
|
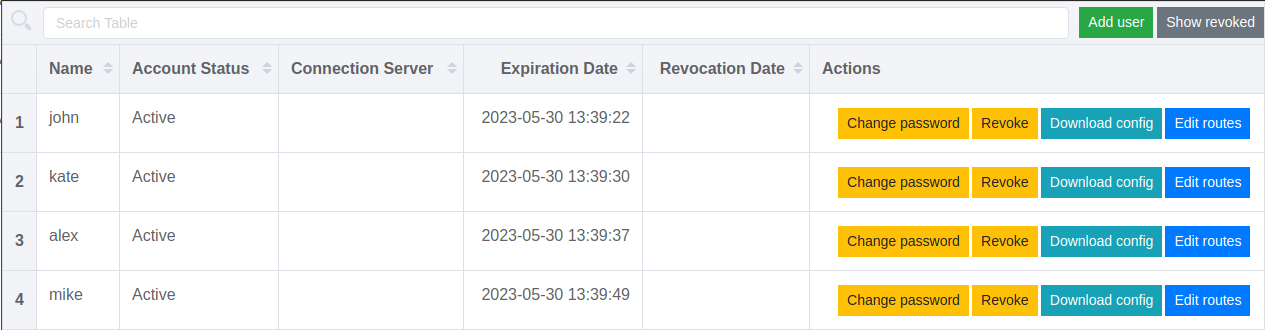
|
||||||
|
|
||||||
An example of dashboard made using ovpn-admin metrics:
|
An example of dashboard made using ovpn-admin metrics:
|
||||||
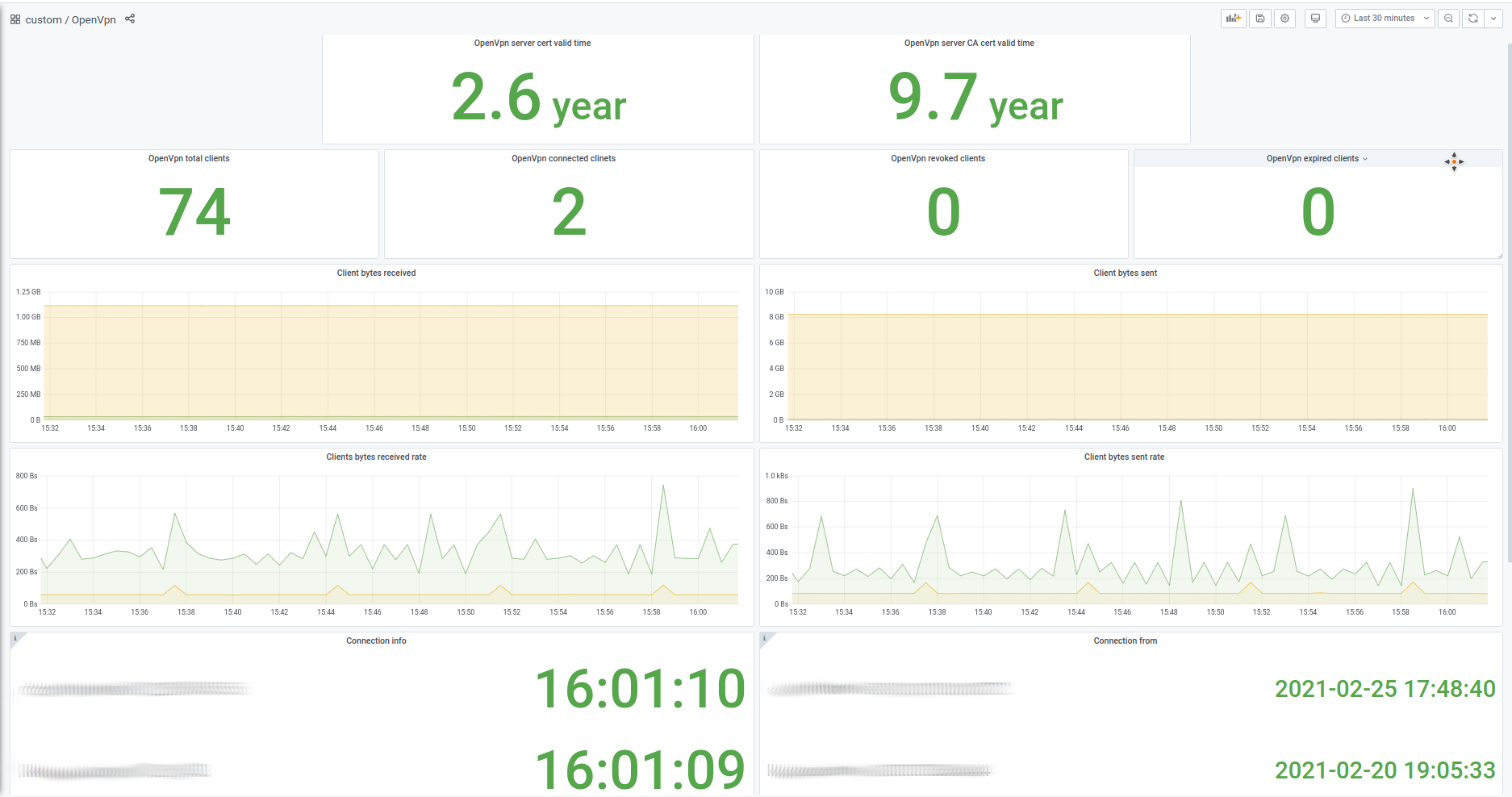
|
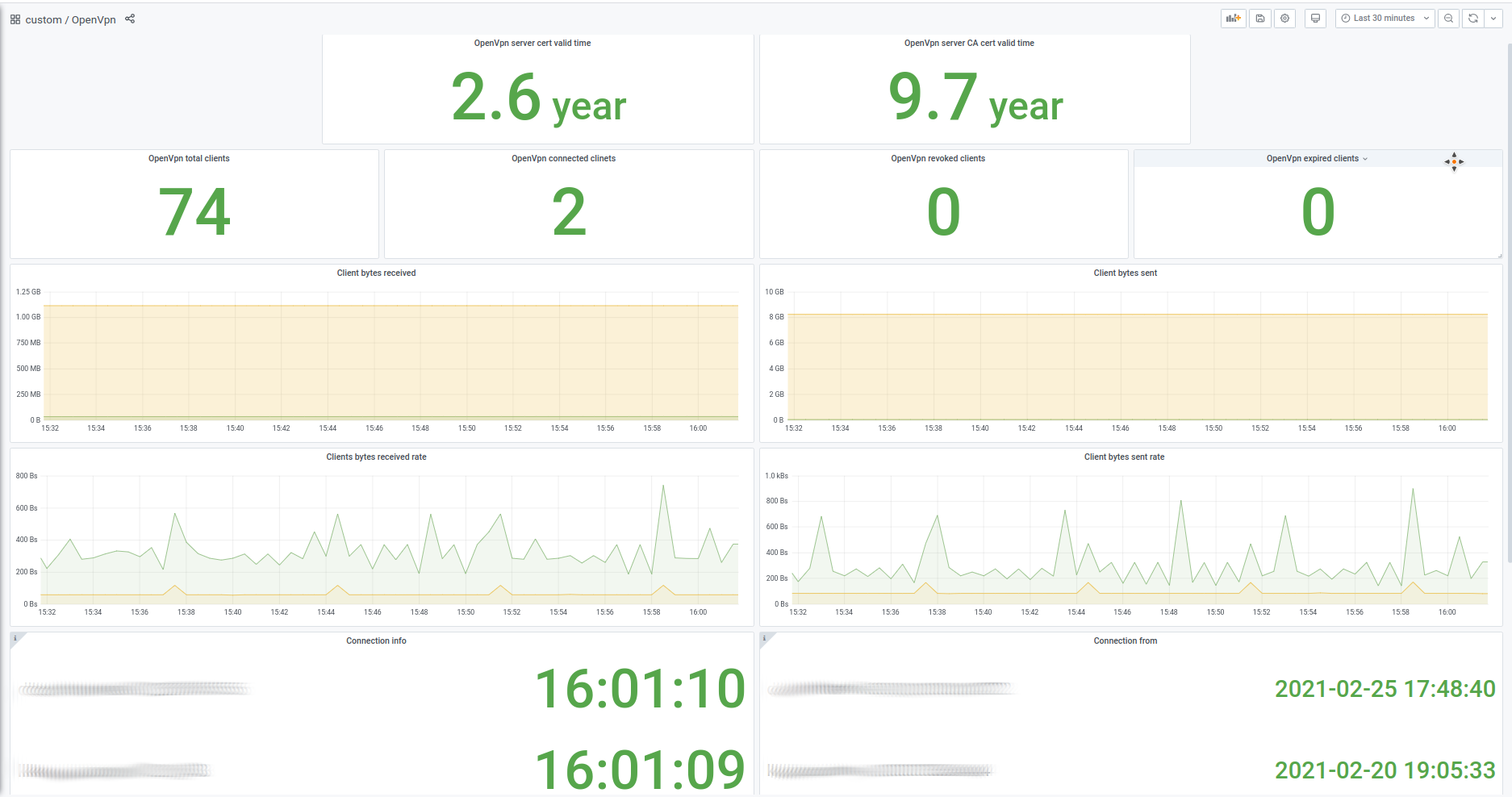
|
||||||
|
|
||||||
## Installation
|
## Installation
|
||||||
|
|
||||||
### 1. Docker
|
### 1. Docker
|
||||||
|
|
||||||
There is a ready-to-use [docker-compose.yaml](https://github.com/palark/ovpn-admin/blob/master/docker-compose.yaml), so you can just change/add values you need and start it with [start.sh](https://github.com/palark/ovpn-admin/blob/master/start.sh).
|
There is a ready-to-use [docker-compose.yaml](https://github.com/flant/ovpn-admin/blob/master/docker-compose.yaml), so you can just change/add values you need and start it with [start.sh](https://github.com/flant/ovpn-admin/blob/master/start.sh).
|
||||||
|
|
||||||
Requirements:
|
Requirements:
|
||||||
You need [Docker](https://docs.docker.com/get-docker/) and [docker-compose](https://docs.docker.com/compose/install/) installed.
|
You need [Docker](https://docs.docker.com/get-docker/) and [docker-compose](https://docs.docker.com/compose/install/) installed.
|
||||||
|
|
@ -36,7 +38,7 @@ You need [Docker](https://docs.docker.com/get-docker/) and [docker-compose](http
|
||||||
Commands to execute:
|
Commands to execute:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
git clone https://github.com/palark/ovpn-admin.git
|
git clone https://github.com/flant/ovpn-admin.git
|
||||||
cd ovpn-admin
|
cd ovpn-admin
|
||||||
./start.sh
|
./start.sh
|
||||||
```
|
```
|
||||||
|
|
@ -54,7 +56,7 @@ Requirements. You need Linux with the following components installed:
|
||||||
Commands to execute:
|
Commands to execute:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
git clone https://github.com/palark/ovpn-admin.git
|
git clone https://github.com/flant/ovpn-admin.git
|
||||||
cd ovpn-admin
|
cd ovpn-admin
|
||||||
./bootstrap.sh
|
./bootstrap.sh
|
||||||
./build.sh
|
./build.sh
|
||||||
|
|
@ -65,7 +67,7 @@ cd ovpn-admin
|
||||||
|
|
||||||
### 3. Prebuilt binary
|
### 3. Prebuilt binary
|
||||||
|
|
||||||
You can also download and use prebuilt binaries from the [releases](https://github.com/palark/ovpn-admin/releases/latest) page — just choose a relevant tar.gz file.
|
You can also download and use prebuilt binaries from the [releases](https://github.com/flant/ovpn-admin/releases/latest) page — just choose a relevant tar.gz file.
|
||||||
|
|
||||||
|
|
||||||
## Notes
|
## Notes
|
||||||
|
|
@ -170,11 +172,6 @@ Flags:
|
||||||
--version show application version
|
--version show application version
|
||||||
```
|
```
|
||||||
|
|
||||||
## Authors
|
## Further information
|
||||||
|
|
||||||
ovpn-admin was originally created in [Flant](https://github.com/flant/) and used internally for years.
|
Please feel free to use [issues](https://github.com/flant/ovpn-admin/issues) and [discussions](https://github.com/flant/ovpn-admin/discussions) to get help from maintainers & community.
|
||||||
|
|
||||||
In March 2021, it [went public](https://medium.com/flant-com/introducing-ovpn-admin-a-web-interface-to-manage-openvpn-users-d81705ad8f23) and was still developed in Flant.
|
|
||||||
Namely, [@vitaliy-sn](https://github.com/vitaliy-sn) created its first version in Python, and [@pashcovich](https://github.com/pashcovich) rewrote it in Go.
|
|
||||||
|
|
||||||
In November 2024, this project was moved to [Palark](https://github.com/palark/), which is currently responsible for its maintenance and development.
|
|
||||||
|
|
|
||||||
10
main.go
10
main.go
|
|
@ -49,7 +49,7 @@ const (
|
||||||
var (
|
var (
|
||||||
listenHost = kingpin.Flag("listen.host", "host for ovpn-admin").Default("0.0.0.0").Envar("OVPN_LISTEN_HOST").String()
|
listenHost = kingpin.Flag("listen.host", "host for ovpn-admin").Default("0.0.0.0").Envar("OVPN_LISTEN_HOST").String()
|
||||||
listenPort = kingpin.Flag("listen.port", "port for ovpn-admin").Default("8080").Envar("OVPN_LISTEN_PORT").String()
|
listenPort = kingpin.Flag("listen.port", "port for ovpn-admin").Default("8080").Envar("OVPN_LISTEN_PORT").String()
|
||||||
listenBaseUrl = kingpin.Flag("listen.base-url", "base url for ovpn-admin").Default("/").Envar("OVPN_LISTEN_BASE_URL").String()
|
listenBaseUrl = kingpin.Flag("listen.base-url", "base url for ovpn-admin").Default("/").Envar("OVPN_LISTEN_BASE_URL").String()
|
||||||
serverRole = kingpin.Flag("role", "server role, master or slave").Default("master").Envar("OVPN_ROLE").HintOptions("master", "slave").String()
|
serverRole = kingpin.Flag("role", "server role, master or slave").Default("master").Envar("OVPN_ROLE").HintOptions("master", "slave").String()
|
||||||
masterHost = kingpin.Flag("master.host", "URL for the master server").Default("http://127.0.0.1").Envar("OVPN_MASTER_HOST").String()
|
masterHost = kingpin.Flag("master.host", "URL for the master server").Default("http://127.0.0.1").Envar("OVPN_MASTER_HOST").String()
|
||||||
masterBasicAuthUser = kingpin.Flag("master.basic-auth.user", "user for master server's Basic Auth").Default("").Envar("OVPN_MASTER_USER").String()
|
masterBasicAuthUser = kingpin.Flag("master.basic-auth.user", "user for master server's Basic Auth").Default("").Envar("OVPN_MASTER_USER").String()
|
||||||
|
|
@ -64,7 +64,7 @@ var (
|
||||||
metricsPath = kingpin.Flag("metrics.path", "URL path for exposing collected metrics").Default("/metrics").Envar("OVPN_METRICS_PATH").String()
|
metricsPath = kingpin.Flag("metrics.path", "URL path for exposing collected metrics").Default("/metrics").Envar("OVPN_METRICS_PATH").String()
|
||||||
easyrsaDirPath = kingpin.Flag("easyrsa.path", "path to easyrsa dir").Default("./easyrsa").Envar("EASYRSA_PATH").String()
|
easyrsaDirPath = kingpin.Flag("easyrsa.path", "path to easyrsa dir").Default("./easyrsa").Envar("EASYRSA_PATH").String()
|
||||||
indexTxtPath = kingpin.Flag("easyrsa.index-path", "path to easyrsa index file").Default("").Envar("OVPN_INDEX_PATH").String()
|
indexTxtPath = kingpin.Flag("easyrsa.index-path", "path to easyrsa index file").Default("").Envar("OVPN_INDEX_PATH").String()
|
||||||
easyrsaBinPath = kingpin.Flag("easyrsa.bin-path", "path to easyrsa script").Default("easyrsa").Envar("EASYRSA_BIN_PATH").String()
|
easyrsaBinPath = kingpin.Flag("easyrsa.bin-path", "path to easyrsa script").Default("easyrsa").Envar("EASYRSA_BIN_PATH").String()
|
||||||
ccdEnabled = kingpin.Flag("ccd", "enable client-config-dir").Default("false").Envar("OVPN_CCD").Bool()
|
ccdEnabled = kingpin.Flag("ccd", "enable client-config-dir").Default("false").Envar("OVPN_CCD").Bool()
|
||||||
ccdDir = kingpin.Flag("ccd.path", "path to client-config-dir").Default("./ccd").Envar("OVPN_CCD_PATH").String()
|
ccdDir = kingpin.Flag("ccd.path", "path to client-config-dir").Default("./ccd").Envar("OVPN_CCD_PATH").String()
|
||||||
clientConfigTemplatePath = kingpin.Flag("templates.clientconfig-path", "path to custom client.conf.tpl").Default("").Envar("OVPN_TEMPLATES_CC_PATH").String()
|
clientConfigTemplatePath = kingpin.Flag("templates.clientconfig-path", "path to custom client.conf.tpl").Default("").Envar("OVPN_TEMPLATES_CC_PATH").String()
|
||||||
|
|
@ -854,7 +854,7 @@ func (oAdmin *OvpnAdmin) getCcd(username string) Ccd {
|
||||||
}
|
}
|
||||||
|
|
||||||
func checkStaticAddressIsFree(staticAddress string, username string) bool {
|
func checkStaticAddressIsFree(staticAddress string, username string) bool {
|
||||||
o := runBash(fmt.Sprintf("grep -rl ' %[1]s ' %[2]s | grep -vx %[2]s/%[3]s | wc -l", staticAddress, *ccdDir, username))
|
o := runBash(fmt.Sprintf("grep -rl ' %s ' %s | grep -vx %s/%s | wc -l", staticAddress, *ccdDir, *ccdDir, username))
|
||||||
|
|
||||||
if strings.TrimSpace(o) == "0" {
|
if strings.TrimSpace(o) == "0" {
|
||||||
return true
|
return true
|
||||||
|
|
@ -1004,7 +1004,7 @@ func (oAdmin *OvpnAdmin) userCreate(username, password string) (bool, string) {
|
||||||
func (oAdmin *OvpnAdmin) userChangePassword(username, password string) (error, string) {
|
func (oAdmin *OvpnAdmin) userChangePassword(username, password string) (error, string) {
|
||||||
|
|
||||||
if checkUserExist(username) {
|
if checkUserExist(username) {
|
||||||
o := runBash(fmt.Sprintf("openvpn-user check --db.path %[1]s --user %[2]s | grep %[2]s | wc -l", *authDatabase, username))
|
o := runBash(fmt.Sprintf("openvpn-user check --db.path %s --user %s | grep %s | wc -l", *authDatabase, username, username))
|
||||||
log.Debug(o)
|
log.Debug(o)
|
||||||
|
|
||||||
if err := validatePassword(password); err != nil {
|
if err := validatePassword(password); err != nil {
|
||||||
|
|
@ -1048,7 +1048,7 @@ func (oAdmin *OvpnAdmin) userRevoke(username string) (error, string) {
|
||||||
log.Error(err)
|
log.Error(err)
|
||||||
}
|
}
|
||||||
} else {
|
} else {
|
||||||
o := runBash(fmt.Sprintf("cd %[1]s && echo yes | %[2]s revoke %[3]s 1>/dev/null && %[2]s gen-crl 1>/dev/null", *easyrsaDirPath, *easyrsaBinPath, username))
|
o := runBash(fmt.Sprintf("cd %s && echo yes | easyrsa revoke %s 1>/dev/null && %s gen-crl 1>/dev/null", *easyrsaDirPath, *easyrsaBinPath, username))
|
||||||
log.Debugln(o)
|
log.Debugln(o)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
2
start.sh
2
start.sh
|
|
@ -1,3 +1,3 @@
|
||||||
#!/usr/bin/env bash
|
#!/usr/bin/env bash
|
||||||
|
|
||||||
docker compose -p openvpn-master up -d --build
|
docker-compose -p openvpn-master up -d --build
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue